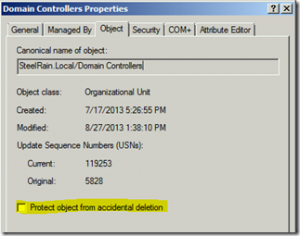
It’s been quite a while since I’ve blogged last, so I’ll start out with a shorter one to re-wet my feet. So by now, it’s pretty common knowledge that if you go to the ‘object’ tab of an object (with the advanced view turned on), you have the option to “Protect Object from Accidental Deletion”
Unfortunately, that checkbox doesn’t exist for DNS zones, at least not in the DNS MMC. A while back, one of my customers had a pretty major outage after one of their primary AD integrated zones got accidentally deleted with a script, which is part of what prompted me to write this.
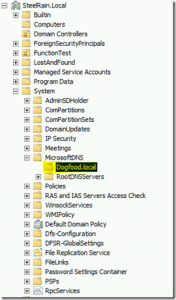
As far as ways to protect DNS zones from accidental deletion using the GUI you *could* use the Active Directory Users and Computers MMC, after turning on the advanced view, assuming that the zones that you want to protect are in the domain partition:
Once you navigate to the zones under MicrosoftDNS, you would see the object tab on the properties of the zone, but what about the zones that live in the DomainDNSZones, ForestDNSZones, or other custom DNS partitions? You could use ADSIEdit, and set the parent / child Deny ACEs for ‘Everyone’, but that’s not much fun. And what if you have thousands of zones, like a lot of my customers? You wouldn’t want to go setting ACEs or checking boxes all day (assuming you had all of your DNS zones stored in the domain partition for some reason).
Fortunately you can use PowerShell to do the job, and there’s a number of different ways that you could do it.
If using PowerShell v2/v3, with the ActiveDirectory module loaded, then you could run the following, modifying the Search Base per DNS partition:
Get-ADobject –filter {objectclass –eq “DNSZone”} –SearchBase “DC=DomainDNSZones,DC=Domain,DC=Com” -properties * | Set-ADObject –ProtectedFromAccidentalDeletion $true
The filters that you use all depend on the zones and/or partitions that you want to target. Also, you’ll likely want to verify that the zones that you query for are in fact the zones that you want to protect from accidental deletion, so take a quick look before piping to Set-ADObject. You’ll also be able to check to see if there are any zones that have already been protected.
Get-ADobject –filter {objectclass –eq “DNSZone”} –SearchBase “DC=DomainDNSZones,DC=Domain,DC=Com” -properties * | ft Name,ProtectedFromAccidentalDeletion -AutoSize
Another reason to verify which zones will be impacted is because some customers use DNS zones for ‘black holes’ to prevent clients from going to malicious sites, so those zones are ones that you’ll likely not want to protect, if they get added/removed frequently.
Also, keep in mind you can do a filter for and protect whatever you want from accidental deletion, it’s not limited to DNS zones; I frequently use it to protect all kinds of things from being deleted during AD health checks. One last thing to remember is that the same rules apply for any object being protected from accidental deletion, meaning that if you want to move an object, you need to unprotect it first, since a move is a delete operation on the source and a write operation on the target. In this case, if you decided to change a DNS Zone from being in the domain partition to the DomainDNSZones partition you’d need to unprotect it first.
Update (3 hours after the original posting): Speaking of protecting other objects, Mike Kline read my latest blog here and mentioned that the ASKDS blog below shows how to do the same thing for other different object classes:
I hadn’t seen that blog before, but what I have does look very similar! :S